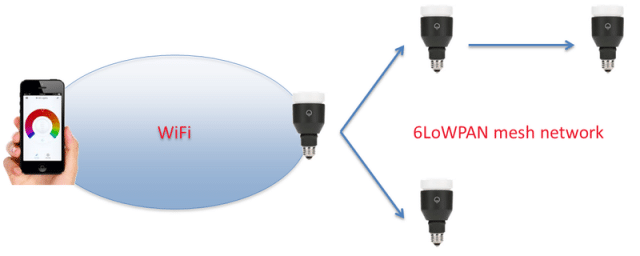
According to a blog post published over the weekend, LIFX has updated the firmware used to control the bulbs after researchers discovered a weakness that allowed hackers within about 30 meters to obtain the passwords used to secure the connected Wi-Fi network. The credentials are passed from one networked bulb to another over a mesh network powered by 6LoWPAN, a wireless specification built on top of the IEEE 802.15.4 standard. While the bulbs used the Advanced Encryption Standard (AES) to encrypt the passwords, the underlying pre-shared key never changed, making it easy for the attacker to decipher the payload.
“Armed with knowledge of the encryption algorithm, key, initialization vector, and an understanding of the mesh network protocol we could then inject packets into the mesh network, capture the Wi-Fi details, and decrypt the credentials, all without any prior authentication or alerting of our presence,” researchers from security consultancy Context wrote.
 |
| BusBlaster JTAG debugger. |
The post underscores the futility of relying on obscurity to prevent hacking attacks. Sadly, the approach, known as security through obscurity, underpins much of today’s Internet of things offerings. Version 1.1 of the LIFX firmware was unavailable for downloads, making it hard for hackers to reverse engineer it and uncover the types of crypto weaknesses that exposed the Wi-Fi credentials. The Context engineers found a way around this hurdle. They undertook the painstaking process of removing the microcontroller embedded inside each bulb and connecting different JTAG pins to special debugging hardware to monitor the signals that were sent when lightbulbs were added or removed to a network. “At this point we can merrily dump the flash memory from each of the chips and start the firmware reverse engineering process,” the researchers wrote.
To its credit, LIFX responded proactively to the discovery by Context. Version 1.3 of the firmware now encrypts all 6LoWPAN traffic using an encryption key derived from the Wi-Fi credentials. It also includes functions for secure processing when new bulbs join a network. But given its warchest of $1.7 million, it’s unfortunate the company didn’t catch the crypto weakness on its own before the bulbs were available for public consumption. Software updates of any type are a hassle for many people, and firmware fixes are often even more difficult or risky.
Marketers would have people believe they’re missing out unless their refrigerators, thermostats, and other traditional appliances are connected to the Internet. Yet over and over, these devices have been shown to introduce networking and privacy threats not present in non-networked iterations. Microsoft, Apple, and Google devote huge amounts of resources to ensuring their wares and services are secure. Manufacturers pursuing Internet of things riches would do well to apportion a similar percentage of their means to securing these devices.