The term ‘Next-Generation Firewall (NGFW)’ was invented by Gartner Research analysts and means using third-generation network firewall technologies in devices. The solutions are based on previous-generation firewalls, the functionality of which was limited only to simple checks and blocking ports/protocols, when necessary. However, since an increasing number of enterprises are now using online applications and SaaS services, simple port and protocol control is not enough to ensure effective network security.
In contrast, new devices have added seamless integration of additional features, such as built-in deep packet inspection (DPI), intrusion prevention system (IPS), and application-level traffic checking (Web Application Firewall). Some NGFWs also include the checking of encrypted TLS / SSL traffic, website filtering, bandwidth control, QoS, anti-virus scanning, and integration with third-party identity management systems such as LDAP, RADIUS, and Active Directory.
Next-generation firewalls are currently categorized as advanced solutions. However, the ongoing massive transition of existing IT systems is publicly available to IaaS cloud platforms, such as Amazon Web Services, Microsoft Azure, and Google Cloud Platform resulting in increasing complexity of hybrid network architectures. This becomes the driving force for further expansion of new-generation firewall capabilities which includes providing advanced traffic management, optimization of WAN, quality of service, and transparent integration of the cloud platform.
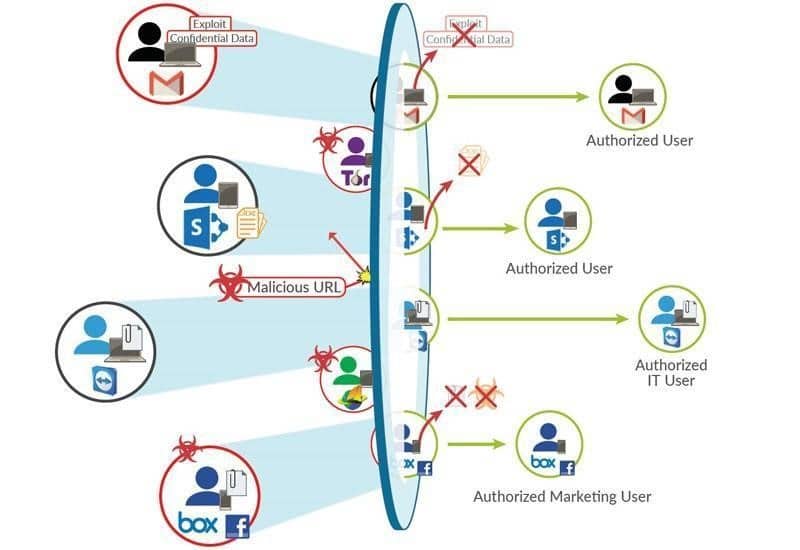
How the Next-Generation Firewall works. Source: Palo Alto Networks
It is worth noting that NGFW provides many tools for automated protection against cyber threats in social networks. As part of anti-phishing protection, these systems can check URLs that are received by company employees and block them if they lead to malicious sites. In addition, NGFW can also analyze attachments that are sent through messages on social networks and prohibit them from access if they contain malicious codes.
Below you can see a brief description of the most popular products in the NGFW segment. More detailed information about the products can be found in the comparison table for NG Firewall at ROI4CIO. It is based on a comparison of leaders (according to Gartner research results).
Contents
Barracuda
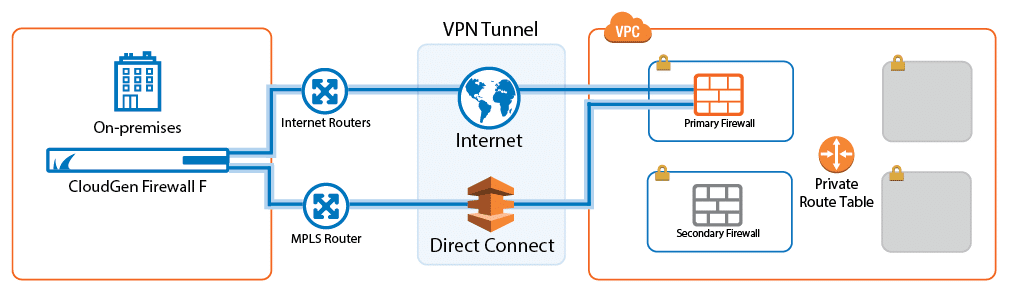
Barracuda CloudGen Firewall is a family of physical, virtual, and cloud devices that are designed to protect the infrastructure of a distributed enterprise network. These types of devices provide enhanced security because they contain the full range of NGFW technologies, including profiling of Level 7 applications, intrusion prevention, web filtering, protection against malware and threats, protection against spam, and access control to the network.
In addition, Barracuda CloudGen firewalls combine advanced fault-tolerant VPN technology with intelligent traffic management and global network optimization capabilities. This helps to reduce linear costs, improve overall network availability, improve interconnection and provide continuous access to applications hosted in the cloud. Scalable centralized management facilitates a reduction in administrative costs for defining and applying granular policies across the entire distributed network.
Barracuda cloud firewalls are best suited for enterprises with multiple branches, managed service providers and other organizations with a complex distributed network infrastructure.
For an immediate response to threats, Barracuda provides Advanced Threat Protection, an integrated cloud service that analyses traffic across all major threat vectors.
Barracuda Advanced Threat Protection provides protection for the company’s infrastructure as well as the ability to detect and block new complex threats without compromising network performance and bandwidth. Advanced Threat Protection is available for all Barracuda CloudGen firewall models.
Some of the main advantages of the Barracuda CloudGen products are as follows:
- Balancing Internet traffic across multiple upstream channels to minimize downtime and increase productivity.
- VPN channel through several broadband connections and MPLS (multiprotocol label switching) replacement.
- Up to 24 physical communication channels to create highly redundant VPN tunnels.
- Accelerated access to cloud applications, such as Office 365, due to the dynamic prioritization of non-critical traffic.
- Guaranteed user access to mission-critical applications through granular policy management.
- Increased channel bandwidth due to built-in traffic compression and data deduplication.
Palo Alto Networks
Palo Alto Networks Next-generation firewalls detect both known and unknown threats (including encrypted traffic) by using data from several thousand installed devices. This approach allows Palo Alto Networks products to prevent a wide range of attacks. For example, these firewalls allow users to access data and applications based on business requirements, as well as prevent identity theft and prohibit hackers from using stolen information.
With the help of Palo Alto Networks’ NGFW, enterprises can quickly create security rules which comply with their business policies and are easy to maintain and adapt to their dynamic environment. They reduce response time through policy-based automatic response. At the same time, IT department can quickly automate workflow by integrating with administrative tools such as ticket creation services or any other system with a RESTful API.
Palo Alto Networks NGFW is supplied both as virtual and hardware devices. For example, the VM series protects private and public cloud environments, providing access to applications and preventing threats. Traffic is classified on the basis of applications, not ports, which gives a detailed view of the threats.
Palo Alto Networks also supplies a wide range of NGFW hardware — from the compact PA-200 model to the super powerful PA-7000 enterprise-level system. The PA-200 is a next-generation firewall in a small form factor that protects networks by blocking a wide range of cyber threats and at the same time ensuring the safe inclusion of applications.
Concurrently, the PA-7000 series combines ultra-efficient software with nearly 700 specialized high-performance processors for networking, security, content inspection, and management.
SonicWall
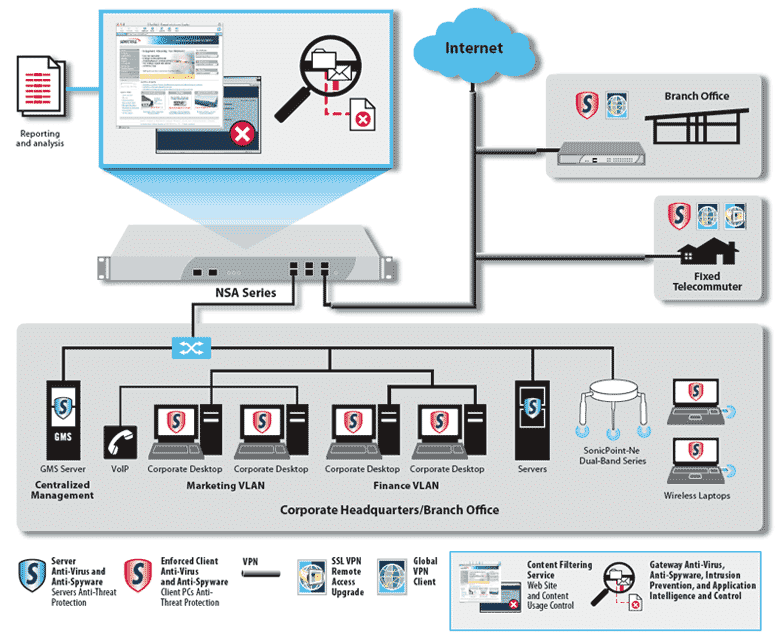
SonicWall offers its customers protection of public, private, or hybrid cloud environments using virtualized versions of new-generation firewalls. SonicWall solutions simplify administration with a common management system for virtual and physical infrastructure.
The SonicWall Network Security (NSA) device series provide medium and large-sized companies with a set of advanced threat prevention features. The NSA series provides automated detection and blocking of attacks in real-time through innovative deep-learning technologies in the SonicWall Capture cloud platform.
NSA Series is distinguished by two basic security technologies that provide a reliable barrier against cyber attacks. Enhanced Advanced Threat Protection (ATP) multiprocessing service is SonicWall’s proprietary Real-Time Deep Memory Inspection Technology (RTDMI). The RTDMI mechanism actively detects and blocks mass and zero-day threats, as well as unknown malware by checking its memory. Thanks to the real-time architecture, SonicWall RTDMI technology minimizes false positives and also detects and mitigates sophisticated attacks when a malware attack takes less than 100 nanoseconds. Furthermore, SonicWall’s patented single-pass packet inspection (RFDPI) engine scans every byte of incoming and outgoing traffic. In addition to the built-in capabilities, the use of the SonicWall Capture cloud platform in the NSA series, including intrusion protection, malware, and web/URL filtering, allows you to block even the most dangerous and insidious threats at the gateway.
Additionally, SonicWall NGFW firewalls provide an additional level of security by performing full decryption and verification of encrypted TLS / SSL and SSH connections regardless of port or protocol. The firewall scrutinizes every packet (header and data) for protocol inconsistencies, threats, zero days, intruders, and even certain specific criteria. The deep packet inspection mechanism detects and prevents hidden attacks that use cryptography, blocks encrypted malware downloads, stops the spread of viruses, and prevents the exchange of data between the affected computer and the control center. Inclusion and exclusion rules allow full control over which traffic is subject to decryption and inspection based on specific organizational requirements and/or legal requirements.
When enterprises activate deep packet inspection functions in their firewalls, such as IPS, antivirus, antispyware software, TLS / SSL decryption/verification, and others, network performance usually decreases, sometimes quite drastically. However, the firewalls of the NSA series are built on multi-core architecture which uses specialized microprocessors. Combined with RTDMI and RFDPI modules, this architecture eliminates the decline of the network systems performance.
Check Point
Today, employees use more applications than ever in their everyday work. This means that if the information security department does not have a specialized means of protection, it has to implement a variety of measures to ensure an adequate level of security. Check Point Next Generation Firewall provides the industry’s largest application coverage — over 8,000 applications and 260,000 social networking widgets. Administrators can create detailed security policies based on users or groups to identify, block or restrict the use of web applications and widgets, such as instant messaging, social media posting, video streaming, VoIP, games, etc.
Seamless integration with leading Identity and Access Management (IAM) systems vendors, such as Microsoft Active Directory, ensures detailed user identification, which can be obtained through:
- integration with IAM or web API providers;
- through the portal;
- by installing a one-time thin agent on the client side.
For a quick analysis of security event data, the developer integrated SmartLog, an advanced log analyzer that provides search results in a fraction of a second. Thus, the department is notified of threats for many millions of log entries in real-time.
Check Point’s unified security management simplifies the monumental task of managing a company’s security environment. The information security department will see and monitor threats, devices, and users using an intuitive graphical interface that provides diagrams and reports on the status of the security system.
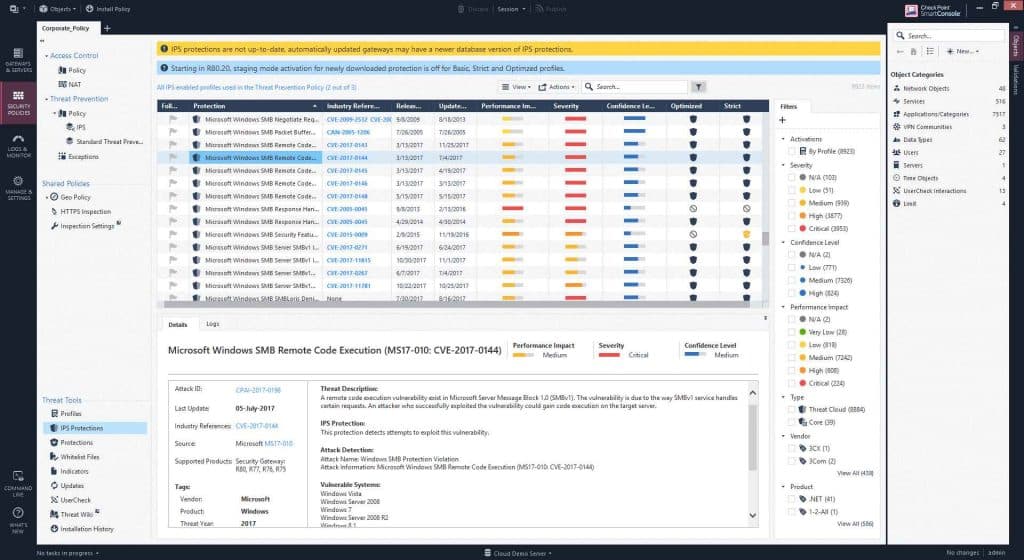
Check Point NGFW contains IPS Software Blade, which protects corporate networks by inspecting packets passing through a gateway. It is a full-featured IPS providing reliable protection against intrusions and frequent automatic updates of the threat definition database. Since IPS is part of an integrated software blade architecture, the customer receives all the benefits of deploying and managing a unified and extensible solution.
Cisco ASA NGFW
Cisco’s next-generation firewalls simultaneously offer a range of unique technologies. First of all, we should mention the Talos service provided by a team of over 250 researchers who analyze millions of threats on a daily basis and create the tools that Cisco NGFW uses to protect against the next large-scale attack. Remember the WannaCry, NotPetya, and VPNFilter epidemics? Talos stopped these mega attacks (along with many others) before they reached their goal, so Cisco NGFW clients automatically received protection.
Cisco NGFWs use built-in advanced security features such as next-generation IPS systems, advanced malware protection, and a sandbox to analyze users, hosts, networks, and infrastructure. They constantly monitor suspicious activity and automatically block it upon finding any.
One more important point which should be mentioned is that Cisco NGFW automates the work of a corporate network and security systems, and this allows information security departments to save time and focus on more pressing tasks. Threat alerts are ranked by importance, so you can stop “shooting at random” and focus on the most important areas. Cisco NGFW works together with the rest of Cisco’s integrated security tools, which allows it to provide information on all attack directions in a timely manner. When this system detects a threat, it automatically blocks it everywhere.
Summary: 5 tips for choosing NGFW products
1. Firewall task No. 1 is to prevent attacks and ensure the security of the customer’s company.
But since preventive measures will never be 100% effective, the NGFW should also offer advanced features for the prompt detection of advanced malware. Therefore, you should choose a product with the following features:
- blocking threats before they get inside the network;
- next-generation high-quality IPS system integrated into the firewall in order to detect hidden threats and quickly neutralize them;
- URL filtering to comply with policies at hundreds of millions of URLs;
- built-in sandbox and advanced malware protection, which continuously analyses behavior of files to quickly detect and eliminate threats;
- own department of antivirus analysts to deal with global threat research and provide the latest updates to NGFW products in order to prevent emerging threats.
2. Full visibility of events on the network.
You cannot provide protection for what you cannot detect. Your firewall should provide a holistic view of network activity allowing you to evaluate:
- activity threats to users, hosts, networks, and devices;
- where and when a threat arose, where else it has been in your extended network, and what the situation is now;
- active applications and websites;
- communication between virtual machines, file transfer, and much more.
3. Flexible management and deployment
Regardless of the customer’s business size— whether it be small, medium, or large — the firewall must meet all the enterprise’s specific requirements.
- On-Demand Management — select this version of the built-in NGFW firewall manager or a centralized control system for all devices.
- Deployment options — on-premise or in the cloud using a virtual firewall.
- Customize features to fit your needs — to get advanced features, you just need to add new subscriptions.
4. Fast detection time
Currently, the standard threat detection time is 100 to 200 days which is too long. The next-generation firewall should be able to:
- detect threats in seconds;
- determine the presence of a successful hack within a few hours or minutes;
- set priorities for attack notifications so that the information security department can quickly and accurately take measures to eliminate threats.
5. Integrated security architecture provides automation and reduces administrative complexity
The next-generation firewall should not be an isolated tool: it should exchange information and work with the rest of the security architecture. Therefore, choose a product that meets the following requirements:
- easily integrates with other tools of the same supplier;
- automatically exchanges data about threats, events, policies, and contextual information with email, endpoint, and network security tools;
- automates security tasks such as impact assessment, setting policies, and user identification.
This review provides a brief description of only 5 NGFW products. More NGFW products and detailed information on them can be found in the NGFW comparison table.