Microsoft has recently released the first test build of Chromium-based Edge Browser and planning to release the stable version soon. One side, the company is striving to level up their web browser’s game, while on the other, Edge Browser and Internet Explorer are creating some serious security issues that could put the data of millions of Windows users at risk.
Microsoft Edge File Permissions Conflicts could Allow XXE Attacks
A recently disclosed Internet Explorer vulnerability is waiting for a fix from Microsoft. Though the company has released a micro-patch to restrict hackers from stealing files or running any surveillance on the victim’s computer, the risk is still there.
Read: Microsoft Releases First Test Build of Chromium-based Edge Browser
A security researcher John Page has discovered an XML External Entity (XXE) security flaw in the browser. He reported the issue to Microsoft on March 27 and also published all the details including the proof-of-concept code on April 10.
Modern web browsers are no longer supporting .MHT files (IE’s web archives format) and so whenever a user tries to open such files, the request got automatically handled by Internet Explorer.
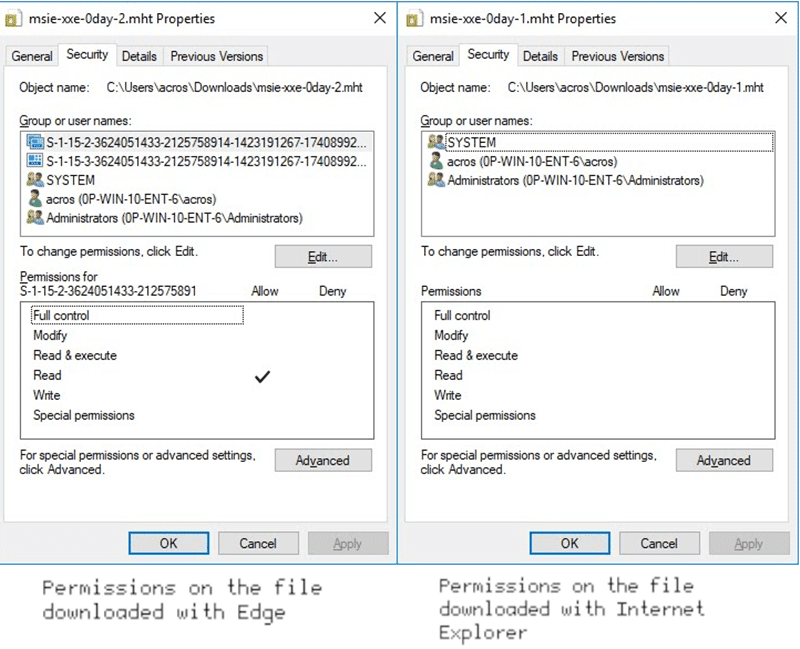
Mitja Kolsek, a security analyst at ACROS, also examined the issue and learned that it’s an “undocumented security feature” in Edge that clashes with IE’s capability to correctly read the mark of the web (MOTW) flag applied to files downloaded from the Internet.
Though Microsoft hasn’t released a fix yet, a micro-patch is available through the 0Patch platform. It’s equipped with error-checking routines that allow Internet Explorer to understand the mark of the web flag Edge sets correctly.
Conflict Between Security Features
MOTW is a security feature that makes sure that Internet Explorer will ask for permission before running active content and local scripts with elevated privileges.
As per the explanation by Microsoft, “In short the MOTW in a page allows the content to run as if from the Internet zone. So the script and active content will have the same privileges as if you were viewing it from a website and not be able to run with elevated access to machine resources.
Mitja also found that the permissions for MHT files downloaded with Internet Explorer are different from those downloaded by Edge. It also appears that MOTW information is stored in the data stream but Internet Explorer faces an error while reading it. The consequences are browser ignores the error and the file gets the same treatment as regular local files, as it doesn’t have the MOTW flag.
It’s also important to note that XXE vulnerability only puts Microsoft Edge users at risk. Page didn’t find any undocumented feature that makes other browsers and email clients vulnerable to exploitation.


