MSI apparently required a reminder that Secure Boot has been standard on PC boards for almost a decade. Over the last several years, MSI has shipped over 300 boards with Secure Boot turned off, as recently uncovered by a security specialist. This makes PCs vulnerable to malicious software, but fortunately, this is something that can be easily fixed by navigating to the BIOS settings of the computer’s motherboard.
Formerly, motherboards’ BIOS systems would simply scan each component in order, from hard drives to RAM to CPUs, prior to actually reaching the Secure Boot phase. At last, it would reach the OS’s initialization bootloader, which would start immediately without further verification. Commonly, cybercriminals would reap the benefits of this straightforward method to preload bootloaders with malware that would then infect the Windows system on subsequent boot cycles.
After the release of UEFI, better known as Unified Extensible Firmware Interface and Secure Boot, in 2011, everything shifted. This has resulted in the storage of an OEM-approved trademark list in non-volatile memory on motherboards. A bootloader that has not been digitally signed will not launch until Secure Boot has been deactivated. According to Dawid Potocki, he found that the MSI firmware on his machine would load operating systems from any source, even if the image lacked a valid digital signature. According to Potocki, motherboards from companies like NZXT, Asus, and Gigabyte do not suffer from the same flaw. If you go to GitHub, you can get a full inventory of the boards that are vulnerable.
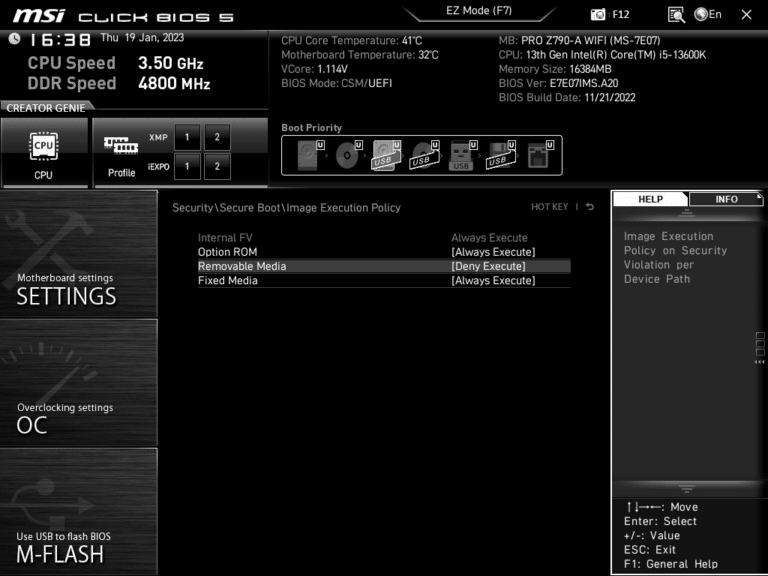
MSI altered its default configuration roughly 18 months ago, which apparently led to the unsecured motherboards. Since then, it has released zero UEFI computers without Secure Boot enabled. At boot time, pushing Delete on an MSI-based machine will bring up the UEFI menu. You may find “Always Execute” set as the standard under Security > Secure Boot. So, it doesn’t matter what kind of digital signature a picture has; the computer will still load it. You must set both Fixed as well as Removable Media to “Deny Execute” if you want your computer to behave in the manner recommended by Microsoft.
MSI didn’t do this by mistake, either. MSI reportedly altered its default configuration to “provide a user-friendly interface,” as claimed by the company’s official Reddit account. It’s a peculiar decision, given that most customers don’t experience any problems and other original equipment manufacturers don’t make the same one. Nevertheless, MSI has chosen to alter future defaults. Updated BIOS files will be made available so that older motherboards may make use of Secure Boot in the future. However, most consumers who use unprotected MSI products won’t go out of their way to see whether there is a vital update available and download it.